For the project I am working on we have a (expensive) development board sitting in the lab, so that everyone in the Team can access it, without the need to have a board for every developer. The board can be accessed by logging in over ssh to the server.
But I thought: Wouldn’t it be nice to be able to access the board like a normal serial adapter on your local computer? I searched a bit and it is doable with pretty much standard software on any Linux/Unix (OSX) system:
The setup looks like this:
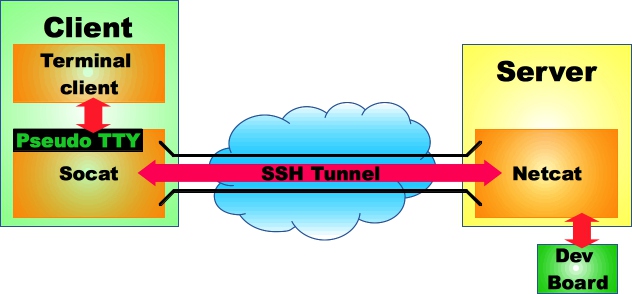
netcat is kind of a Swiss Army Knife regarding networks. On the our Server netcat listens for a connection on a TCP port on the loopback interface, so that the port is not visible from the outside (which otherwise might invite unintended guests ;). The inputs and outputs of netcat are redirected to the Serial Port where the Dev Board is connected to.
Socat is similar to netcat, as it can connect to servers over the network, but has a couple of extra features, for example creating a pseudo terminal device: All the data that is written to the Pseudo Terminal device is sent out over the network. And everything that is received from the network is written to the Pseudo Terminal. Again Socat is set up to only connect to the loopback interface, so that the Port is not visible from the internet.
Finally a SSH tunnel connects the two computers and tunnels the data to the ports on the loopback interfaces.
All this can be initiated from the client like so:
ssh -fCo "ExitOnForwardFailure yes" -L 54333:localhost:54321 USER@SERVER "nc -l localhost 54321 </dev/ttyDEVBOARD >/dev/ttyDEVBOARD" && socat pty,link=$HOME/vmodem0,wait-slave tcp:localhost:54333 & screen ./vmodem0 BAUDRATE
Here 54321 is the Port on the Server side (on which netcat listens), and 54333 is the port on which socat on the Client side listens. SSH is told to start netcat on the client side and to fork into the background when it is done. Also the Tunnel is set up to use compression. When the SSH Tunnel was set up successfully, socat connects to the tunnel, where on the other side netcat is already listening and creates a pseudo terminal device in my /home directory. Every terminal client can connect to this device as if it was a physical device locally attached to the Client. In my case I am using GNU screen as a terminal client.
The only problems that I had is that sometimes the start up of the connection fails. But other than that, once the connection is established, it is as stable as a normal ssh connection.
